Scanning
We run nmap tool on ports 53, 80, 88, 135, 139, 389, 445, 464, 593, 636, 1433, 3268, 3269, with script and software versions:
Enumeration
We access the web service, we find the corporate intranet:
Here you can see news and alerts, indicating that NTLM access has been disabled.
Now, we found a register users forms:
Here we are told that we can contact you to change the user's password, the password will be the same as the user's password.
We review the documentation in the page "salesorders.html", we see that it leaves us a software usage guide where it connects to port 4411.
Exploitation
We see that it is indeed operational, but checking the nmap we see that the port was not open.
We use the smbclient.py tool, but we see that we cannot connect through smb.
So I tried to request a TGT for the user, so I could try to connect via Kerberos ticket.
We tried to connect to the machine with the ticket, but it seems that we cannot write to any resource and we cannot connect to the psexec.py tool.
We now try to connect through the mssql service and we see that we are inside. We reconfigure some options to be able to execute "xp_cmdshell" and we are able to execute commands in the machine.
We try to read the user flag, but we see that we do not have permissions on the files of the user "miscsvc".
So we created credentials in SecureStrings format, executed commands impersonating the identity of the user "miscsvc" and managed to read the user flag:
Our user does not have privileges, but let's remember that the user "miscsvc" does, since he belongs to the IT group:
Access the "Apps" directory and find the software with the same name as the machine (causality? I doubt it very much).
Reviewing functionalities of the application, it seems that there is a function called "UploadOrder", which allows to upload commands and since we saw at the beginning that command injection was possible, we could execute commands remotely in a combined way and with a payload compatible with .NET technology.
We try to use classic commands like "help", "info", but we get the same error, so we try to try a command injection and we see that we get code execution.
We go back to the previous steps and try to check the user "ksimpson", in case he has not changed the password and it is the same as his name. And we see that they work:
We use the smbclient.py tool, but we see that we cannot connect through smb.
So I tried to request a TGT for the user, so I could try to connect via Kerberos ticket.
We tried to connect to the machine with the ticket, but it seems that we cannot write to any resource and we cannot connect to the psexec.py tool.
We try to get the TGS (Ticket Granting Services) tickets and list the user "sqlsvc":
We obtain the ticket of the user "sqlsvc", export it to an environment variable and try to connect via Kerberos with the mssqlclient.py tool, but we see that it does not work.
We try to generate a silver ticket, but for this we will need to convert the password to "nthash", get the "domain sid", the "domain", a valid SPN and set the "user id" to 500. Some of this information we already have, so let's go for what we don't have.
Converting the password to NTLM format::
We now try to connect through the mssql service and we see that we are inside. We reconfigure some options to be able to execute "xp_cmdshell" and we are able to execute commands in the machine.
We try to read the user flag, but we see that we do not have permissions on the files of the user "miscsvc".
We list the tables belonging to the database:
Privilege Escalation
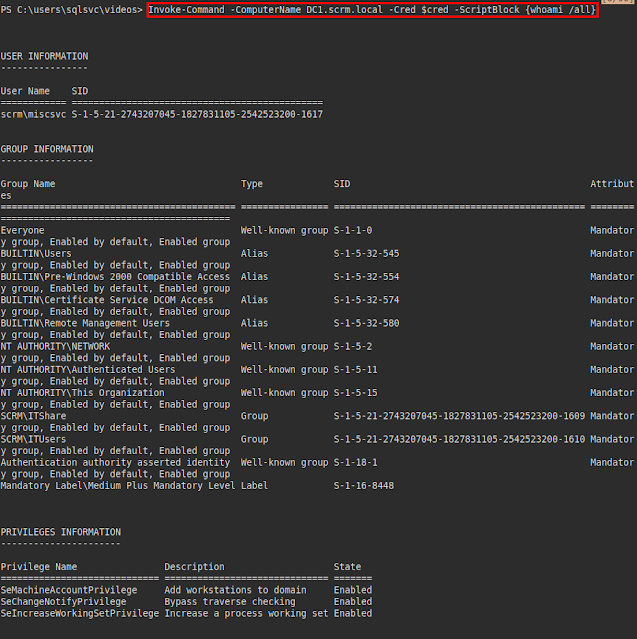
We run a "whoami /all" on the user and see that we belong to interesting groups such as "ITShare" and "ITUsers":We reviewed the shares, found several, but the one from the IT department caught our attention:
Our user does not have privileges, but let's remember that the user "miscsvc" does, since he belongs to the IT group:
Reviewing functionalities of the application, it seems that there is a function called "UploadOrder", which allows to upload commands and since we saw at the beginning that command injection was possible, we could execute commands remotely in a combined way and with a payload compatible with .NET technology.
So I searched among my notes how to generate specific payloads for this technology, I found the ysoserial tool. We use this tool to serialize in base64 the execution of a netcat to our attacker machine (remember, I previously uploaded a netcat to have a more stable session ;)):
About
David Utón is Penetration Tester and security auditor for web and mobiles applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks.